Overview
Hightouch's AWS integration powers several features:
- Workspace deployment on AWS (see Regions)
- Self-hosted storage via S3
- Athena source
- S3 source
- S3 destination
- AWS PrivateLink
Setup
To give Hightouch access to resources on your AWS account, go to the Cloud providers tab on the Settings page. Click Add cloud provider, and select Amazon Web Services.
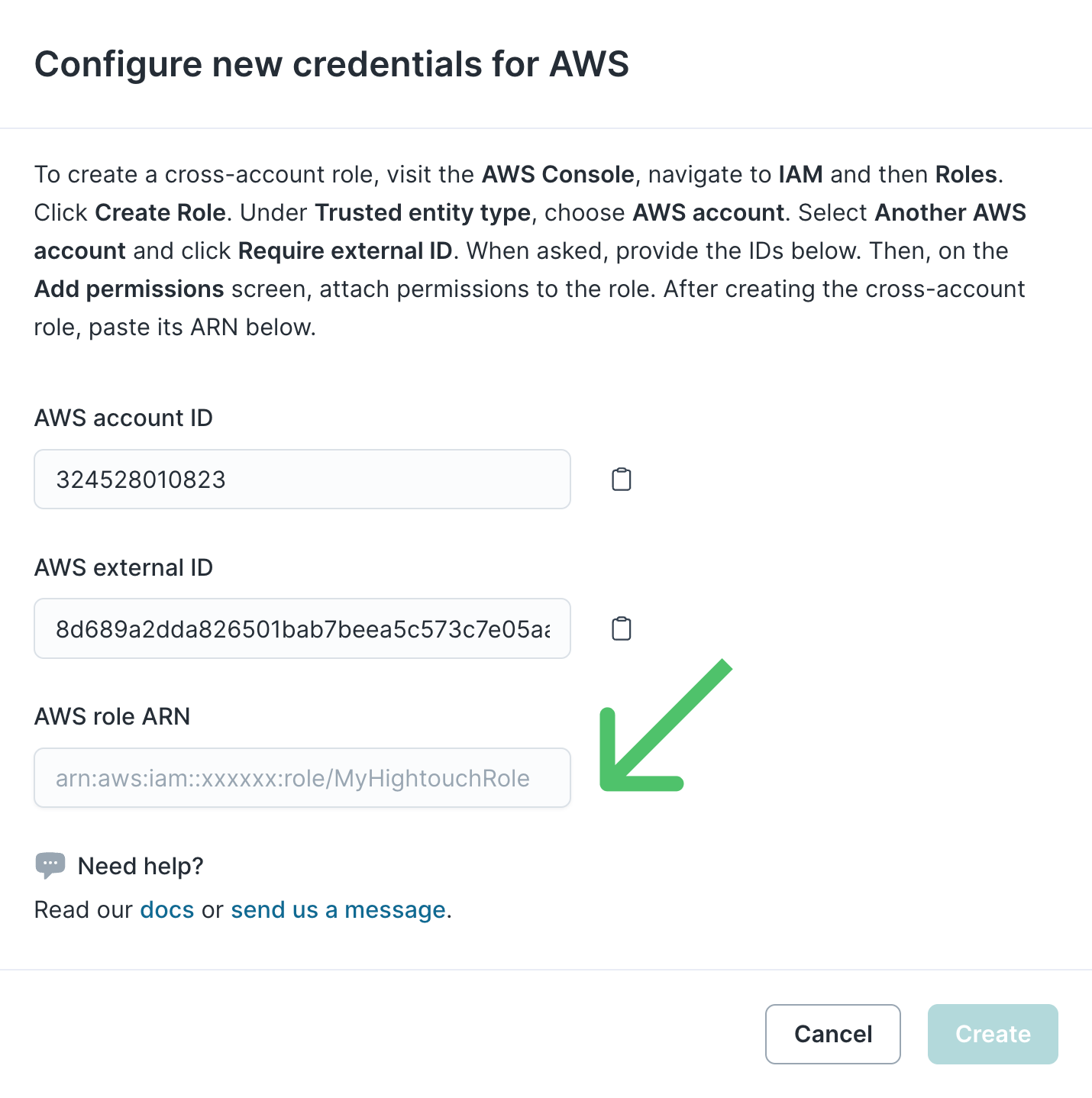
Give your credential a Display name, then select either Cross-account role or Access key.
Cross-account role
Cross-account roles are a mechanism provided by AWS to allow you to grant secure access to Hightouch without requiring that you hand over sensitive secrets like Secret Access Keys.
The Hightouch UI displays an AWS account ID and a randomly generated AWS external ID, as shown below, which you need to enter into an IAM Role you create in your AWS account. Store these values for future reference.
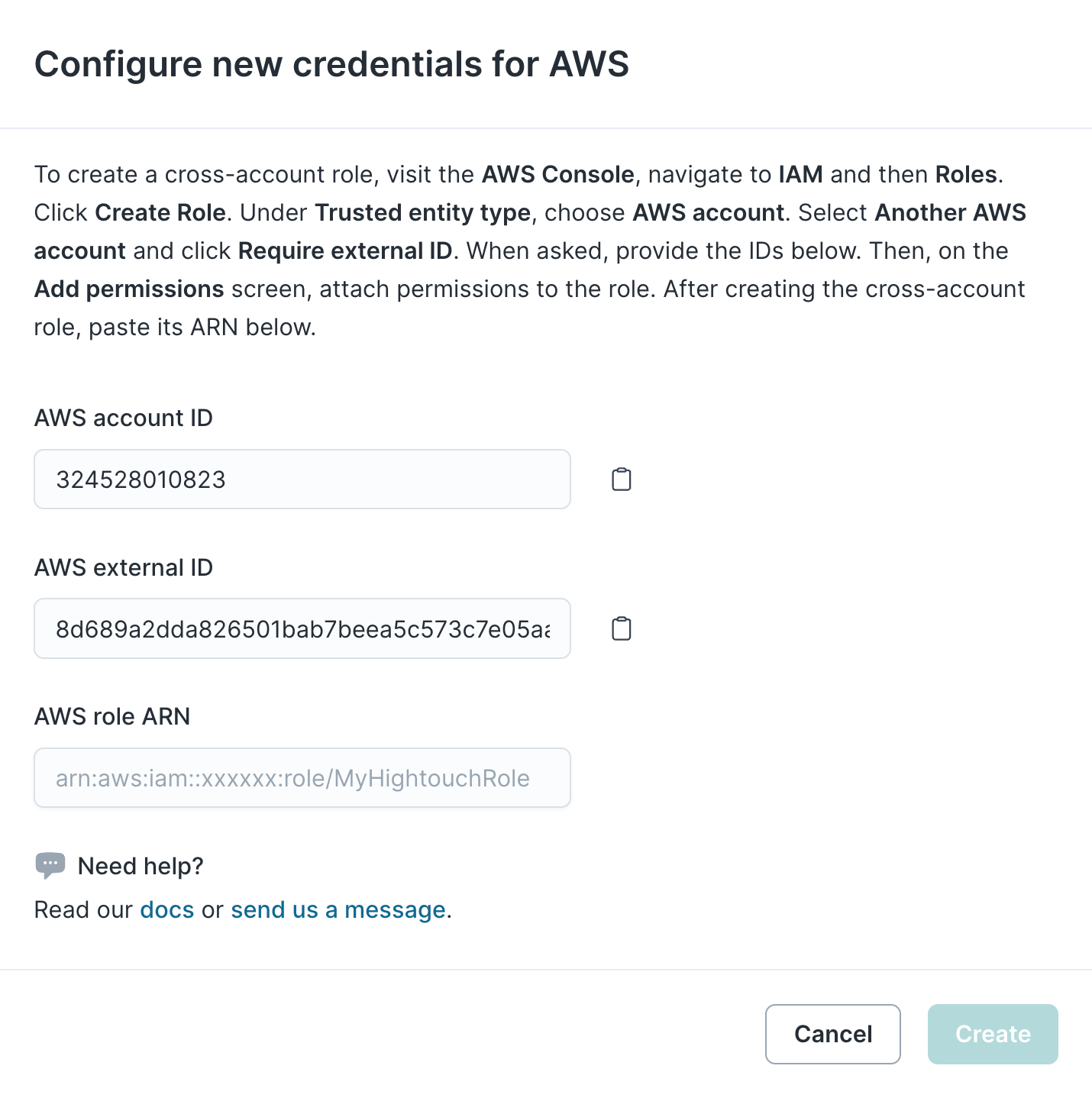
Neither the Account ID nor the external ID are secrets, so you don't need to worry about securely storing them.
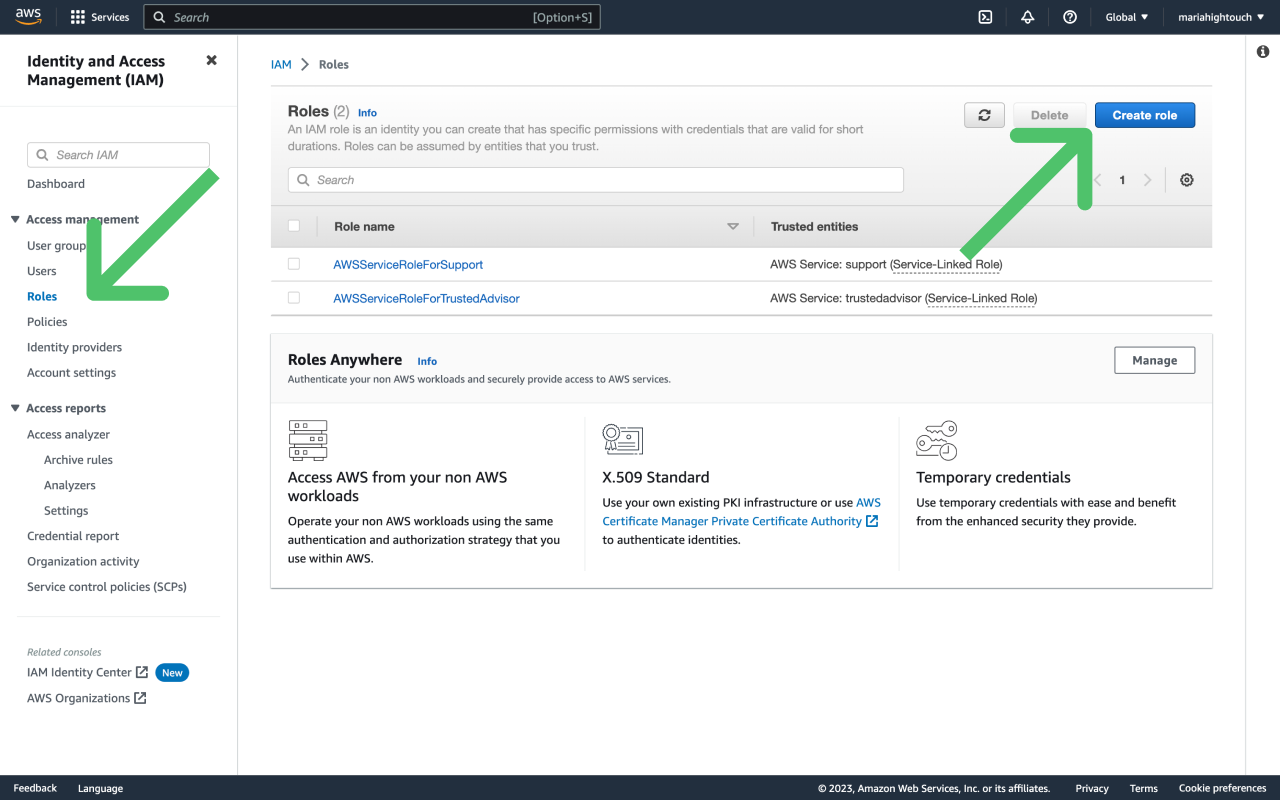
- From your AWS console, navigate to Identity and Access Management (IAM) > Access Management > Roles and click Create Role.
- Under Select type of trusted entity, choose AWS account. Then under An AWS account, select Another AWS account.
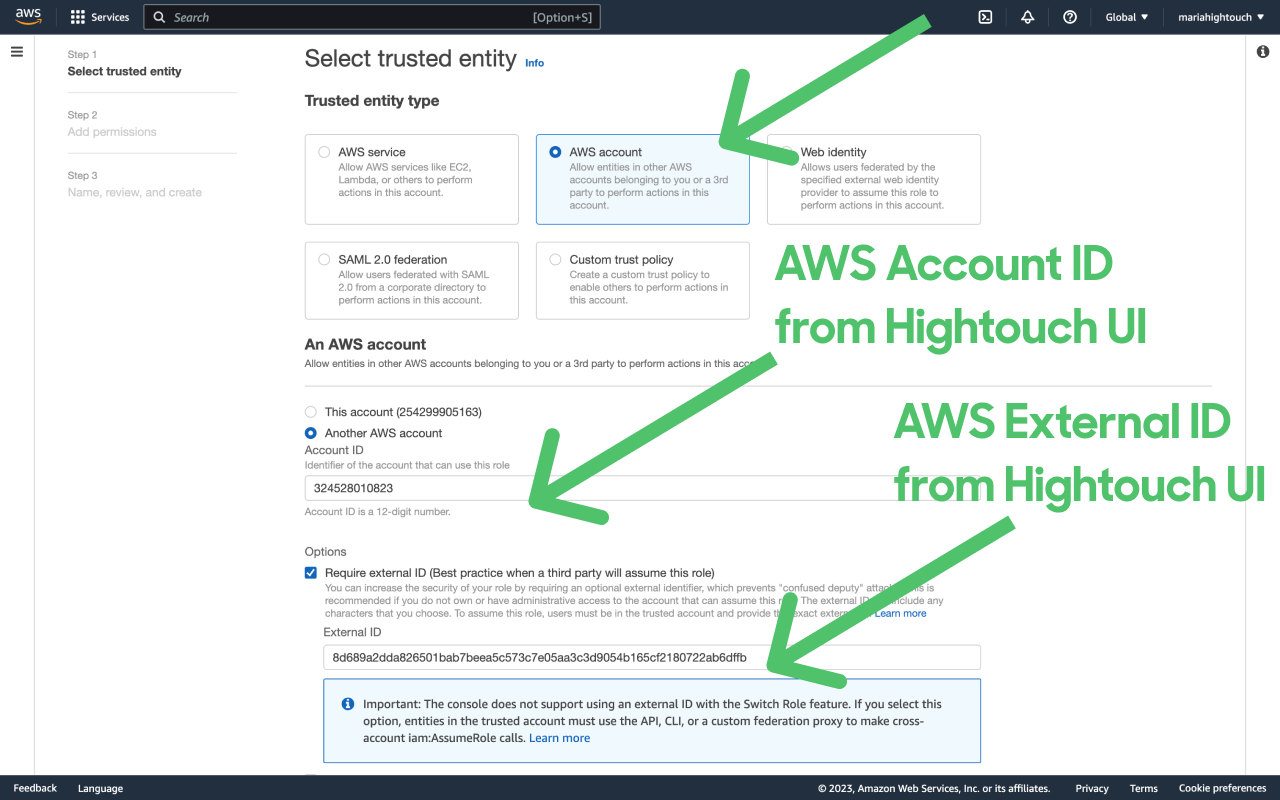
- Enter the Account ID you copied from the Hightouch UI, select Require external ID and enter the external ID you copied from the Hightouch UI. Click Next.
- Attach permissions to the role, choose a role name, then click Create role. The exact permission policies you attach depend on which Hightouch features you intend to use. Consult the documentation for those services for further guidance.
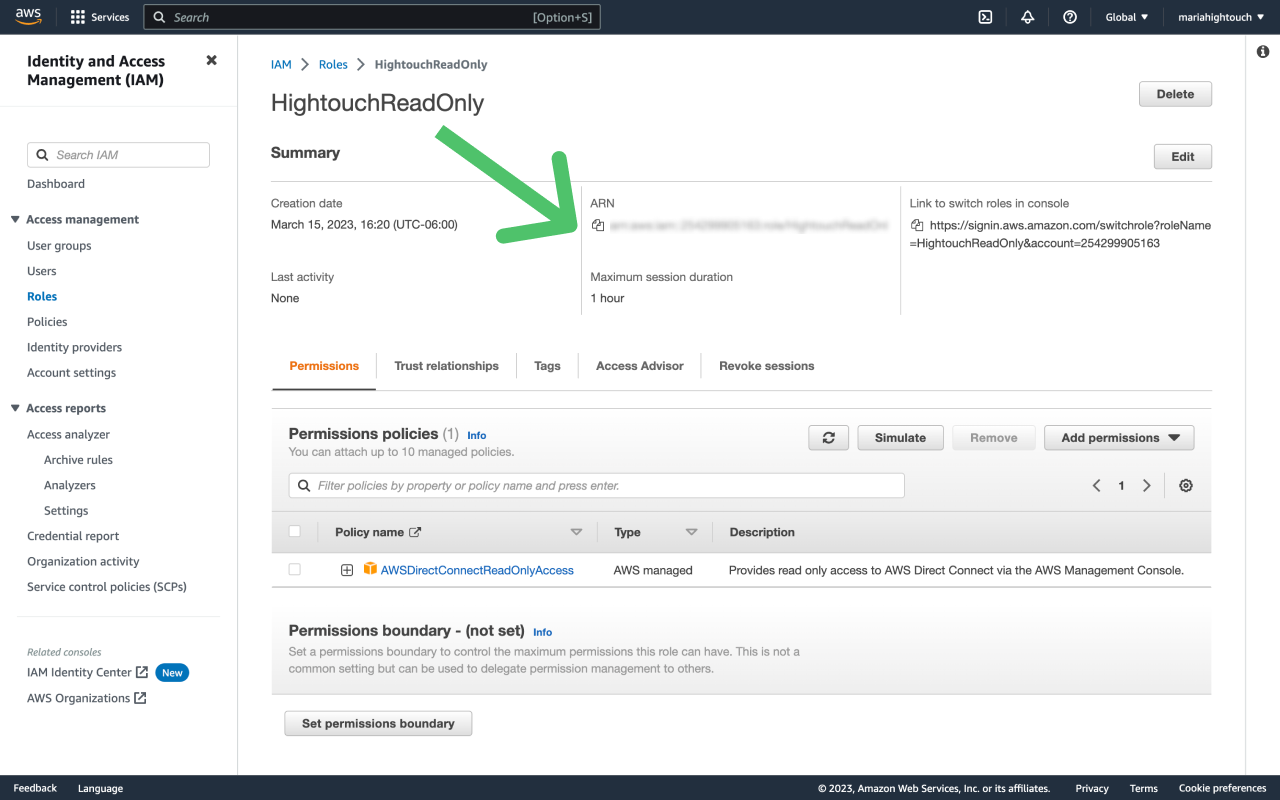
- Copy the Role ARN from AWS IAM and paste it into the Role ARN field in Hightouch. Click Create to complete the process.
For more information, read AWS's tutorial on delegating access cross-account using IAM Roles.
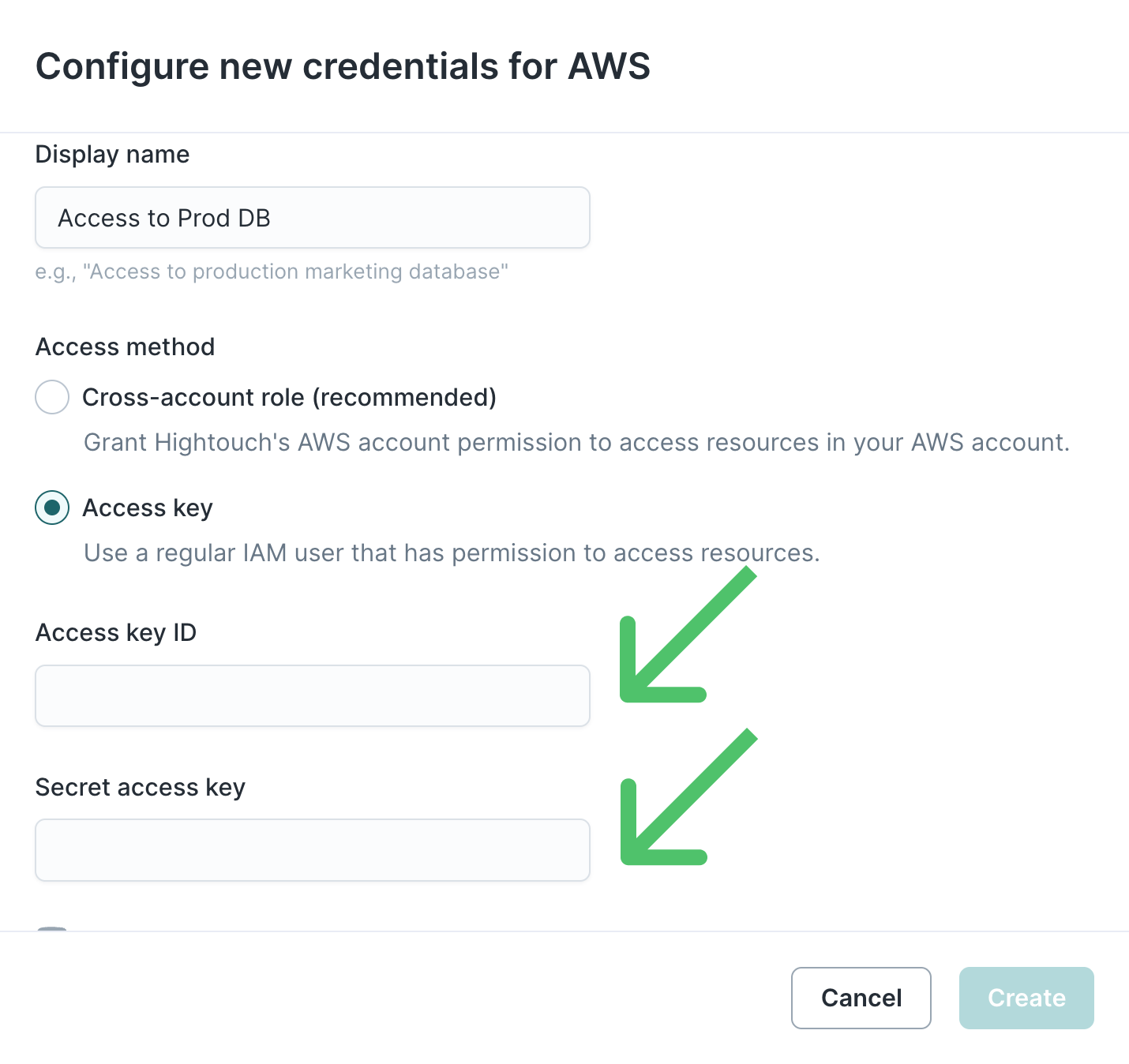
Access key
The Access Key access type allows you to configure Hightouch to use an IAM user by providing the user's Access Key ID and Secret Access Key.
If you need help generating these keys, consult the IAM article on this topic.
Once you have an Access Key ID and Secret Access Key, paste those values into the form and click Create.
Tips and troubleshooting
CredentialsError: Missing credentials in configuration
If you receive the following error CredentialsError: Missing credentials in config, it means Hightouch can't assume the role required by your Athena or S3 sync, or external storage configuration.
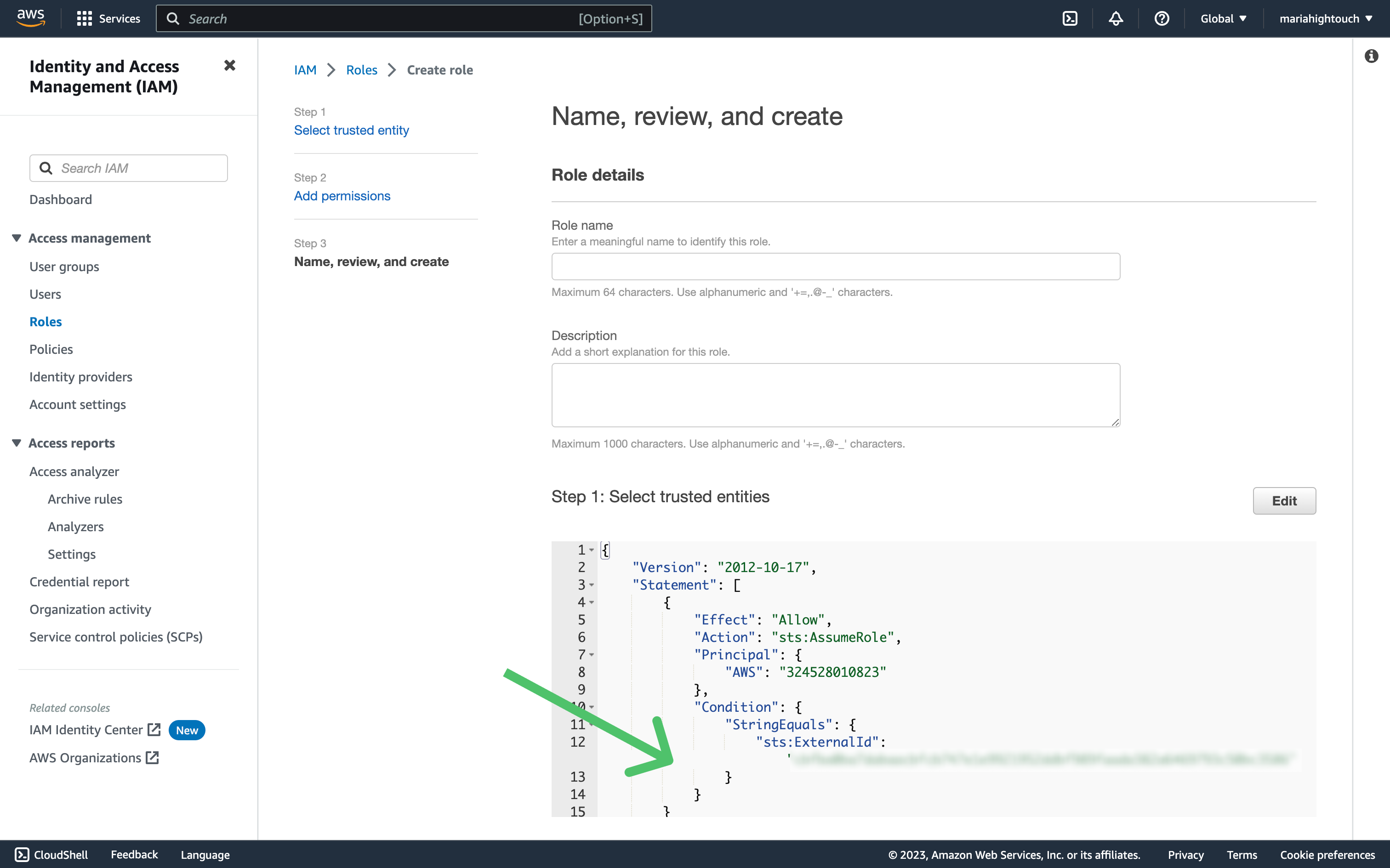
This error is often due to an issue with the IAM trust policy. This policy defines which other AWS accounts can assume roles in your account. When you set up AWS credentials in Hightouch using a cross-account role, we provide you with Hightouch's Account ID and an additional external ID. You should include Hightouch's Account ID in your role trust policy, and can optionally include the external ID.
To troubleshoot this error, follow these steps:
- Ensure that the role exists.
- Ensure that the role has a trust policy attached.
- Ensure that the role's trust policy includes our Hightouch AWS account ID (
324528010823) as a principal. - If the role trust policy includes an external ID check, ensure it matches the external ID generated by Hightouch. See the example below:
If you want to check the external ID but misplaced the external ID that Hightouch generates, you need to re-create the cloud provider integration in Hightouch. Hightouch only displays this value once during cloud provider setup.