Hightouch powers mission-critical processes for some of the largest brands in the world, including the NBA, Warner Music Group, GameStop, AXS, and Spotify. Hightouch doesn’t store any data, but instead makes it easy to collect, unify, and activate data from your existing data warehouse. This gives Hightouch incredible power and flexibility, because you have easy access to all of your data.
With this wide-ranging access, however, proper governance is critical. Enterprises consistently choose Hightouch not just because of our powerful features, but also because of our flexible tooling for access control, change management, incident response, and more.
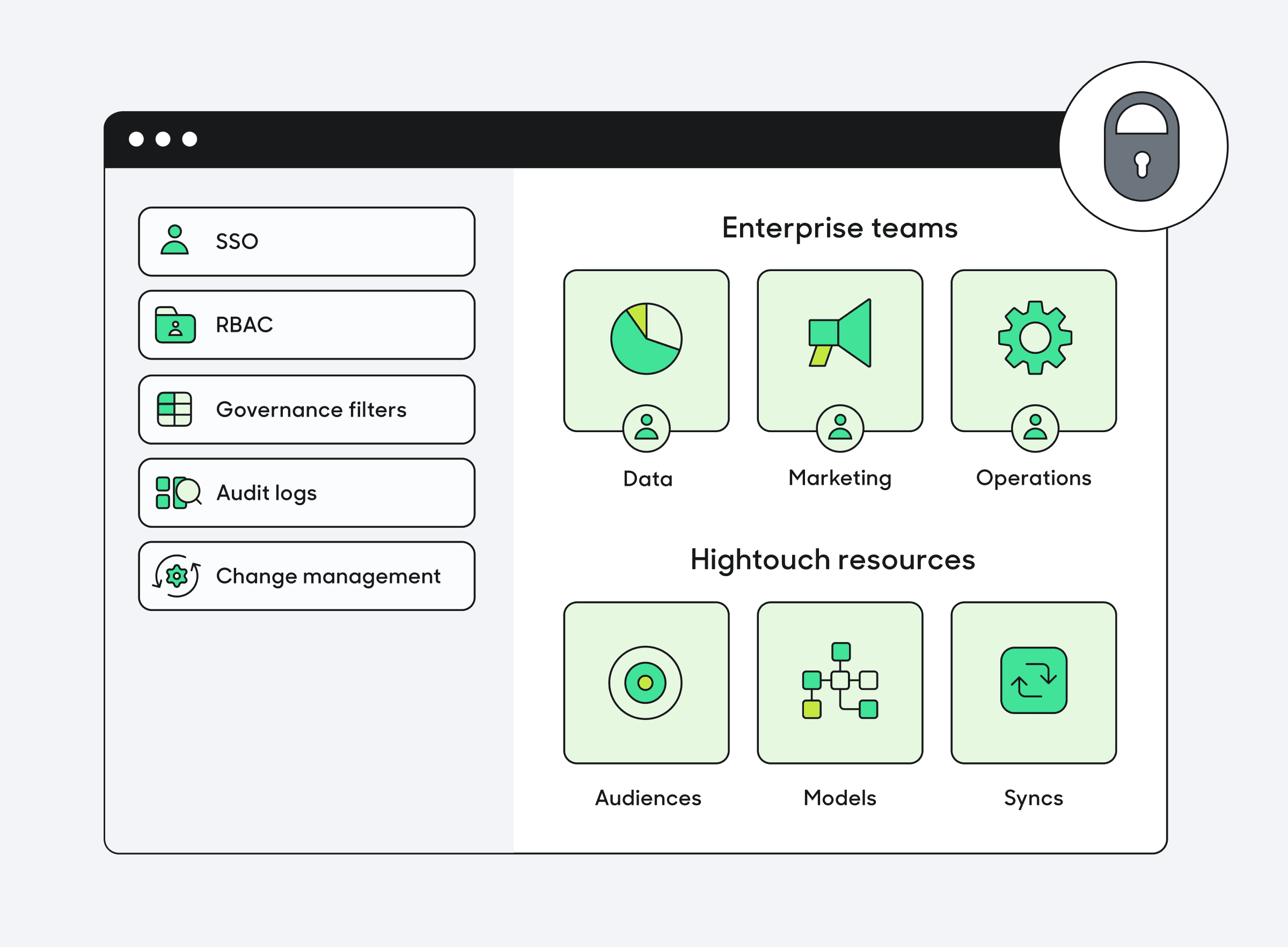
Platform governance in Hightouch
With Hightouch serving as a bridge between the entire data stack and complex business end systems, we’ve built our platform to be enterprise-ready on day one. Read on for a summary of some of the key features that support enterprise companies.
Role-based Access Controls (RBAC)
Different users at enterprises will use Hightouch for different things– and have different levels of clearance to access potentially sensitive data. Our Role-Based Access Control (RBAC) system is easy-to-use via a self-service UI, but flexible enough to fully manage how individual users can access Hightouch and your underlying data.
Access is managed through two key variables:
- Custom roles: Define each type of user and the set of permissions that the user has to different workspaces and resources. By default, Hightouch offers an “Admin” and “All Users” role, but you can create as many custom roles with custom permissions as you need. Furthermore, you can assign users to as many roles as necessary.
- Resource-based access control: Granularly manage access to specific resources such as data sources or data destinations. For example, you could give a
Advertisingrole permission to set up data syncs to Google Ad Manager, but prevent them from syncing data to HubSpot.
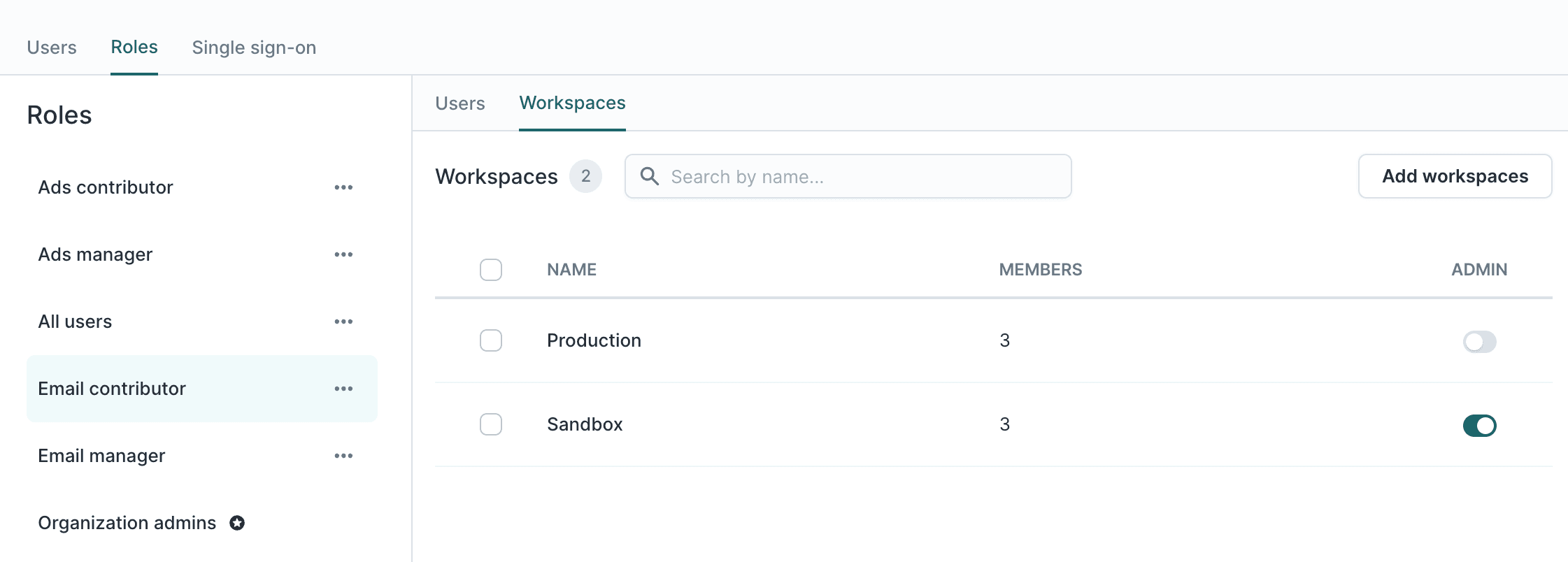
Create custom roles that you can assign to users across workspaces.
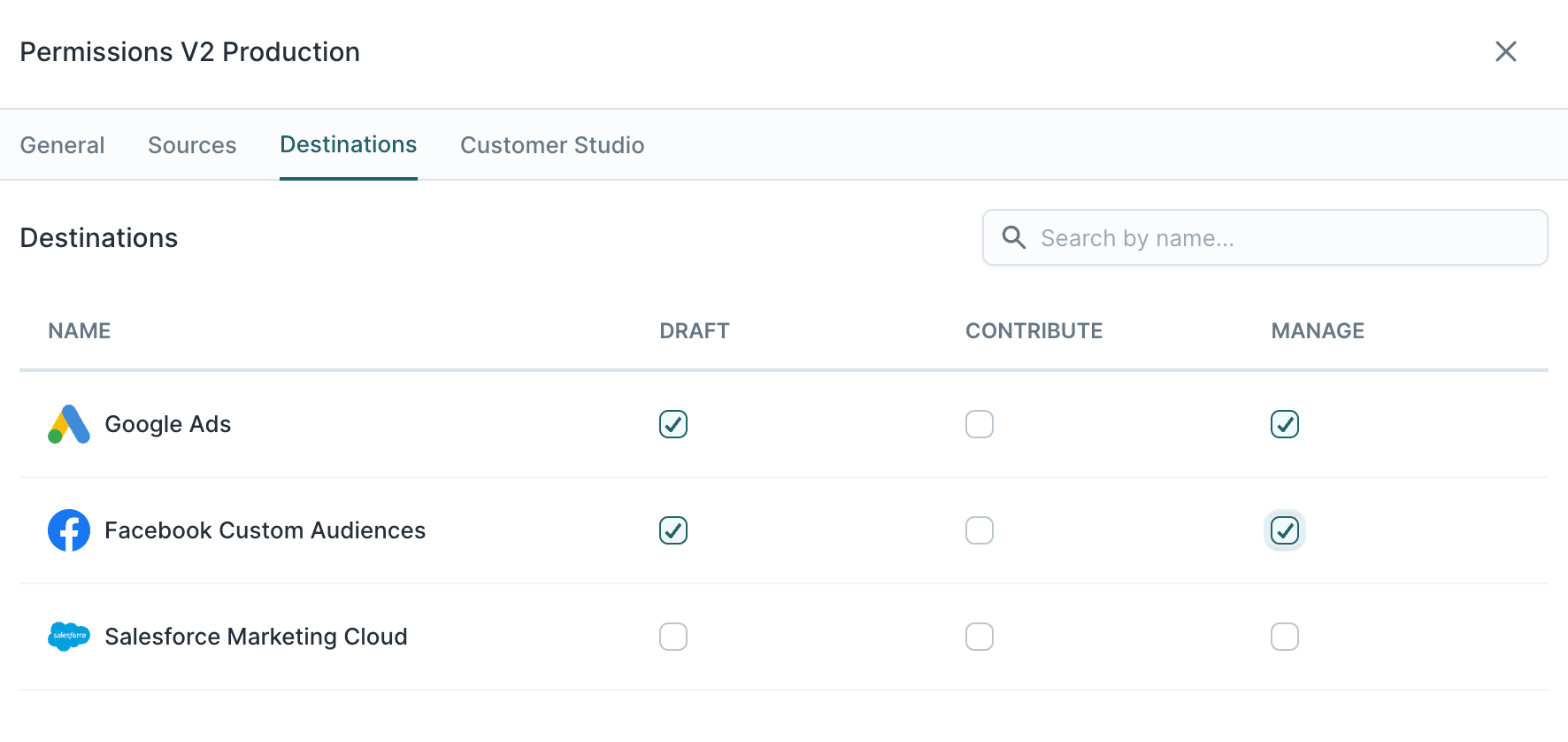
Manage access for each source or destination, for each role.
Our role system makes it easy to manage how teams and individual users interact with Hightouch and your underlying data. Beyond just governing access, you can also use roles to customize what types of alerts different groups of users receive, to make sure that people only receive the critical alerts that matter to their business function and don’t “tune out” because they’re receiving irrelevant notifications.
Subsets: Row-level access
It’s most effective to directly manage access for sensitive data at the source–that data itself– rather than within the context of user roles. Our Subsets feature allows organizations to grant access to data based on the attributes of that data itself, such as:
- Geography. Data security and privacy requirements vary from country-to-country– and is particularly regulated through the European Union. Directly manage how data within each geography can be used, and who should be allowed
- Business Unit. Conglomerates and multi-brand companies can easily partition data by business unit to ensure that only the correct employees can access each business unit’s data.
- Marketing Consent. You can universally prevent your Hightouch users from accessing or using data from customers who have opted out of marketing, by setting up row-level filters based on consent fields in your data.
These are just a few examples of how to manage access to data based on the data itself. You can create your own Subset rules based on whatever data attributes matter to your organization.
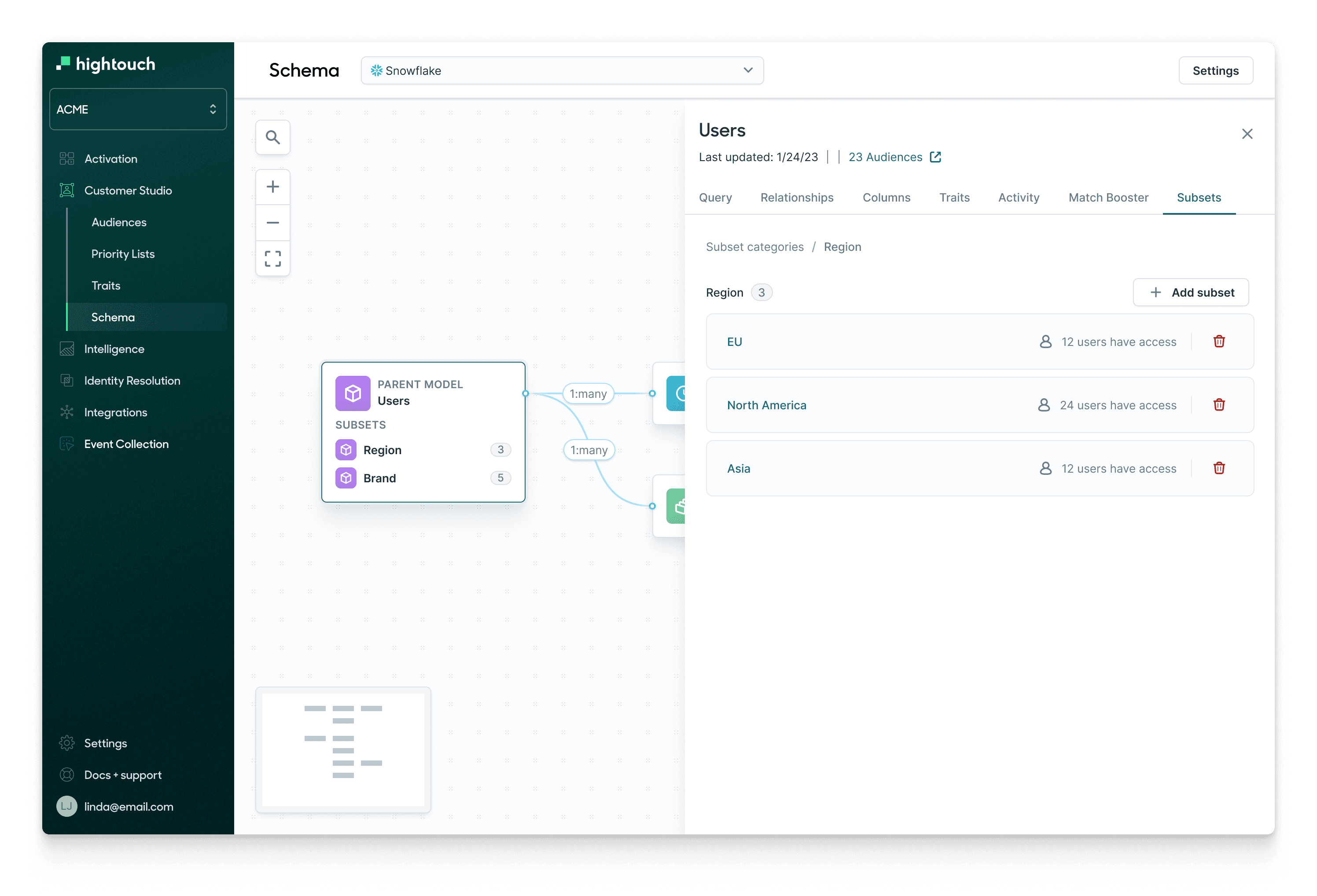
Companies can set Subsets based on properties of their data. For example, this company partitions their data by different regions, and grants access to that regionalized data to different user lists.
Read the Subset docs here.
Destination Rules: Row-level sync controls
Destination rules enable organizations to specify which rows can be synced to particular destinations based on attributes within the data. This row-level governance allows for granular consent management.
For example, you might have customers that have opted in to email marketing, but not to SMS. You can set up a rule so that those customers are never synced to your SMS destination, regardless of their inclusion in an audience that’s synced there.
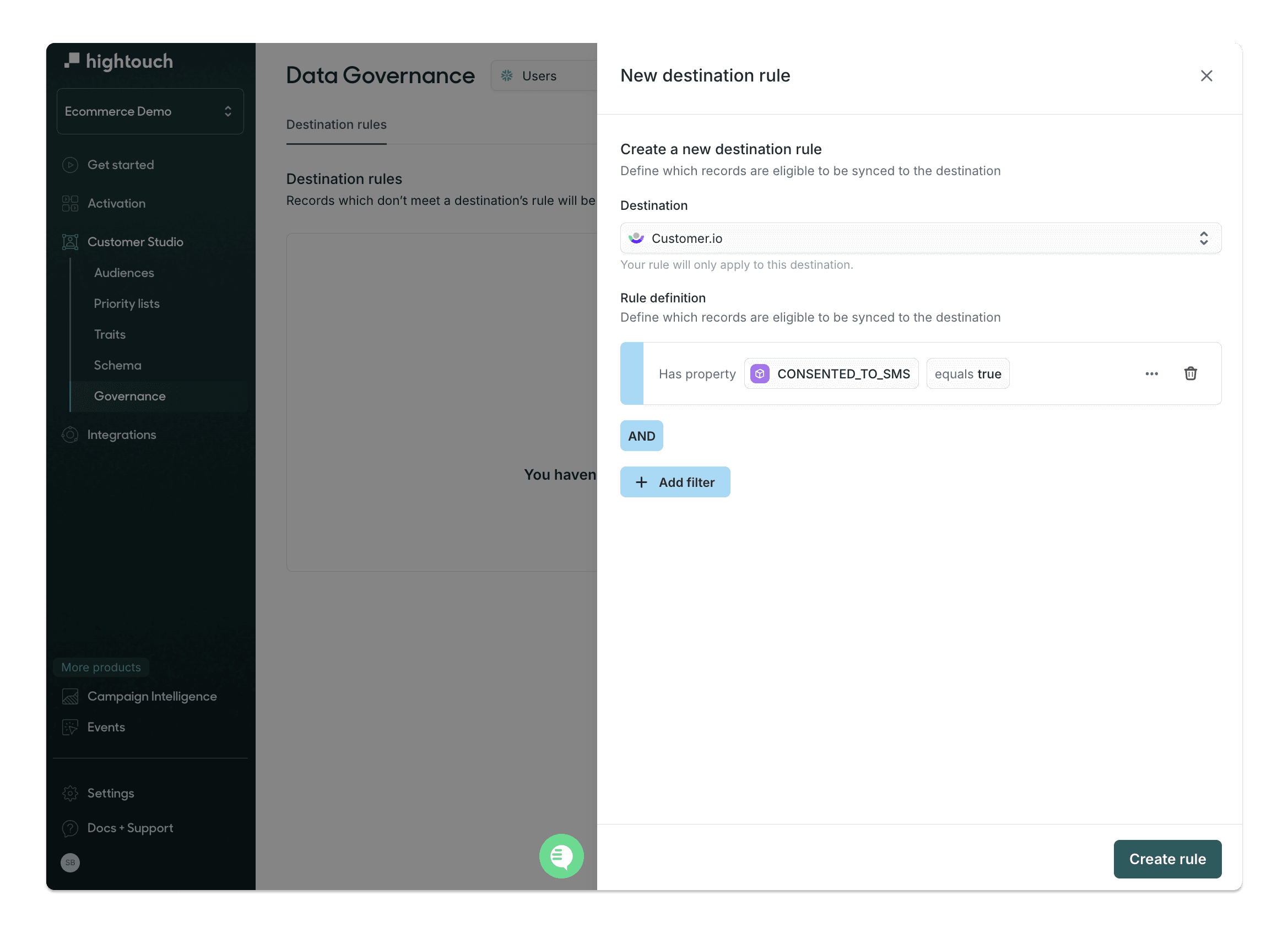
Companies can use Destination rules to control which rows can be synced to specific destinations based on attributes within the data.
With destination rules, you can build a single audience to sync to multiple destinations, and trust that only compliant data will be synced.
Read our destination rules documentation here.
Audit Logs
Audit logs make it easy for users to browse, filter, and search through a historical log of in-app activity for troubleshooting and auditing purposes. You can inspect all changes to your account’s resources—syncs, models, audiences, sources, destinations—along with user sessions, query previews, and other key actions.
For example, if a user changes a sync that results in sending erroneous data to a downstream tool, an admin can simply search the audit logs for the impacted tool and review the recent changes made to the sync. The admin can respond quickly and deter similar incidents from happening again.
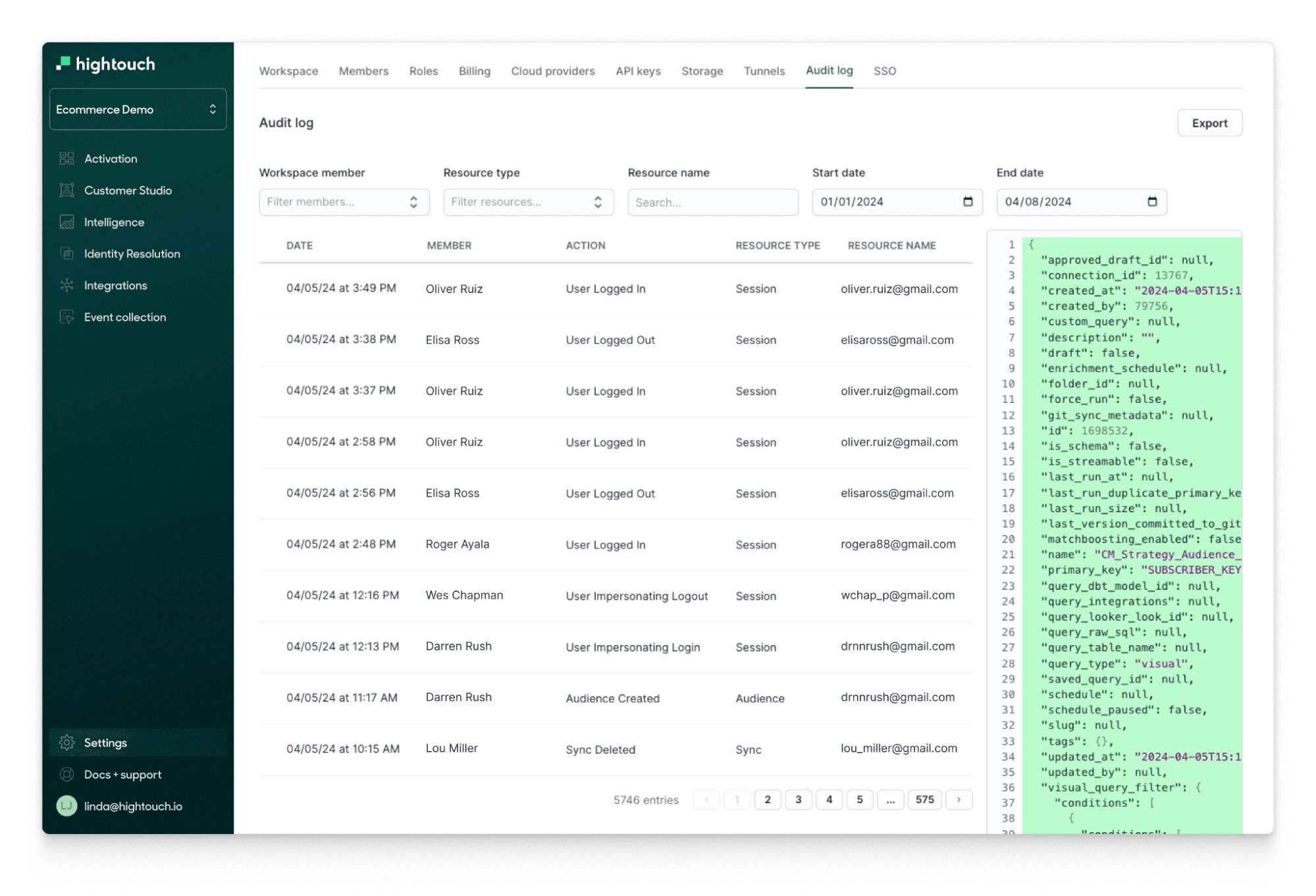
Audit logs UI
We also write back sync logs to your data warehouse, which make it easy to audit and debug your syncs. We have an easy-to-use live debugger in our app; warehouse sync logs take that same data and makes it available in your data warehouse to explore using SQL or BI tools. For example, you can:
- Categorize all the errors in your sync using regular expressions and find unexpected errors.
- Filter out previously failed rows from your model using a JOIN.
- Aggregate the sync history to see what rows are changing the most.
- Visualize row changes in your models over time. For example, you may be interested in seeing how targeted users in an ad campaign changed over the campaign duration.
Read our audit logs documentation here, and warehouse sync logs documentation here.
Change Management
At an enterprise scale, the impact radius of a bad sync can be serious, negatively affecting internal teams, customers, and brand equity. Hightouch offers several key features to help you manage change and prevent errors in production:
- Approval Flows require specific users to receive in-app approval before any syncs can go into production.
- Sync Templates allow companies to pre-define approved source and destination settings. These can allow team members to launch new data-driven initiatives quickly, bypassing lengthier approval flows for their pre-approved sync templates.
- Git Sync allows technical teams to manage version control via Git.
- Environments provides a visual interface to manage staging and production deployments for non-technical users.
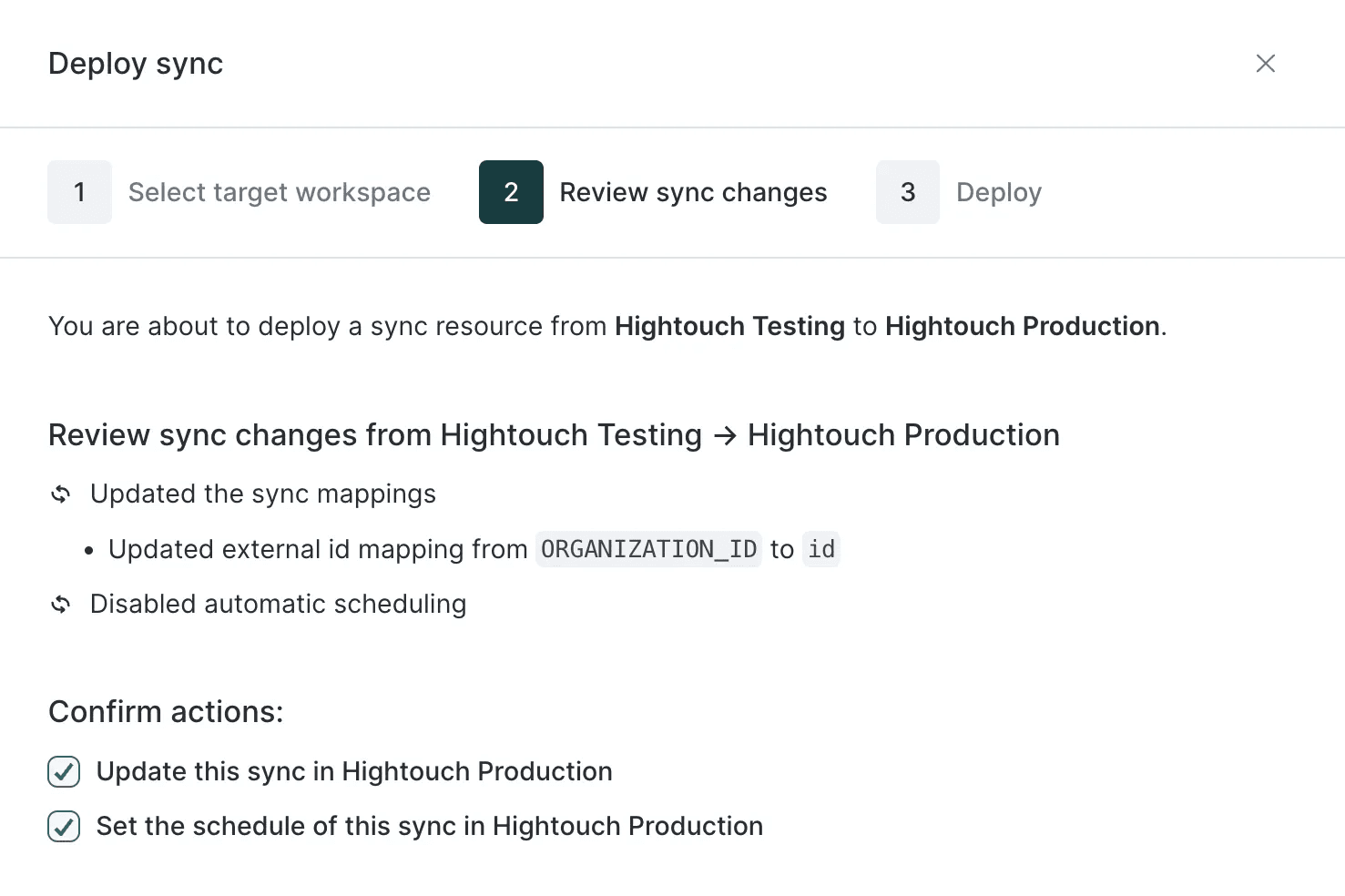
Deploy changes between different environments in Hightouch.
Read our approval flows documentation here, git sync documentation here, sync template documentation here, and environments documentation here.
Single Sign-On (SSO)
Single Sign-On makes it easy for enterprises to manage Hightouch access across all of their users. Hightouch supports third-party identity providers (IdP) such as Okta and Microsoft Entra ID (formerly known as Azure Active Directory), all through a simple in-app interface.
- Creating user accounts: SAML SSO provides just-in-time (JIT) provisioning– so Hightouch can seamlessly create new accounts new accounts for authorized users whenever they first try to sign in.
- Updating user accounts: SAML SSO updates users each time they log in with Hightouch. You can also opt into SCIM (System for Cross-domain Identity Management”) to automatically sync with your identity provider whenever changes to a user’s profile occur. This can be useful for automated deprovisioning.
- Managing group access: Admins can map groups in their identity provider to specific workspaces and roles in Hightouch. For example, a user in the
Marketingteam in Okta can be mapped to theAudience Editorrole in Hightouch.
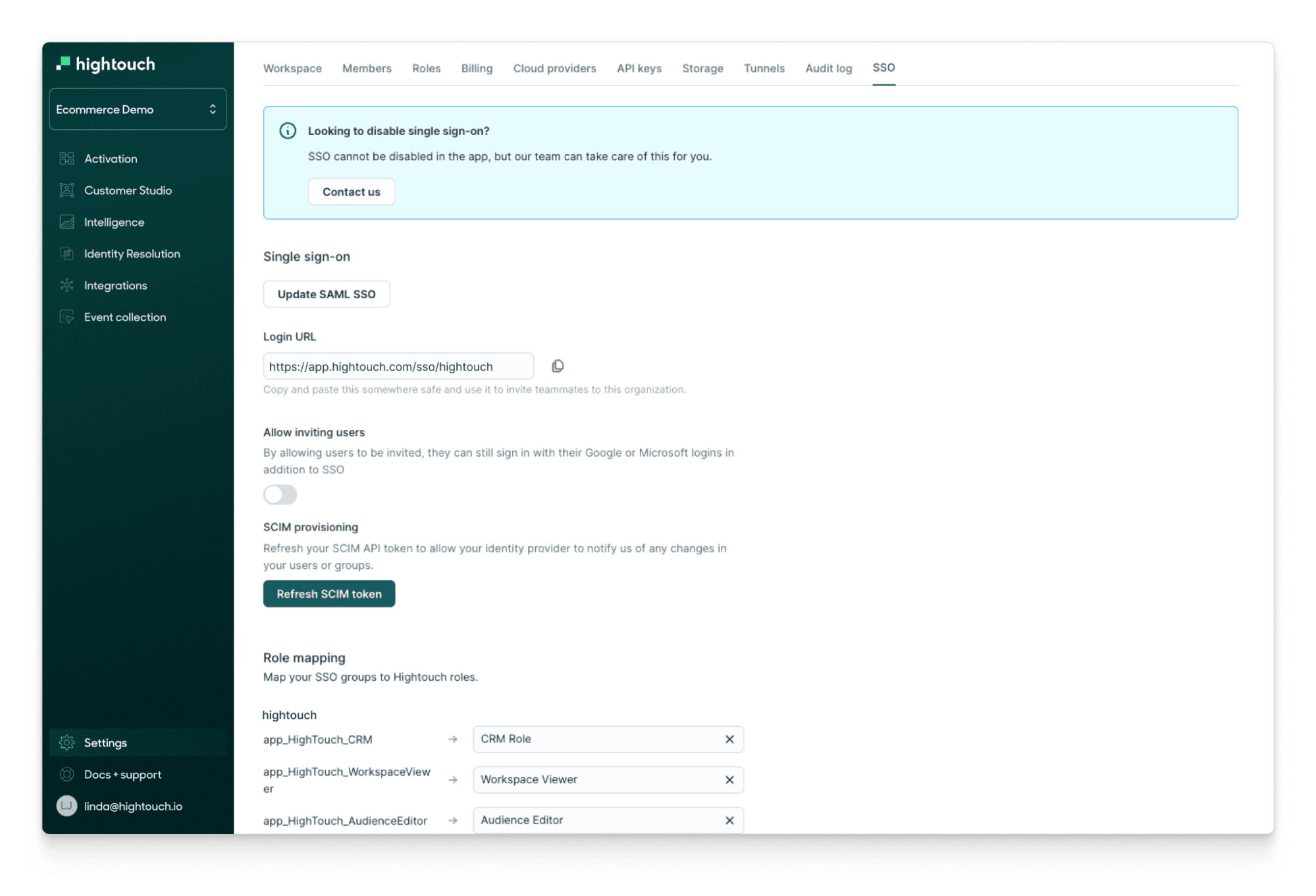
Enabling SSO in-app
Read our SSO docs here.
Getting Started
Hightouch is trusted by enterprises around the world to power millions of dollars of ad spend, marketing automation, internal workflows, alerting, and product experiences, among many other use cases. Reach out if you’re interested in learning more, or check out our docs for more information.

















