We don’t store your data
Hightouch is more secure because no duplicate storage is required. Instead, we simply read from your data warehouse, where your data stays safe and sound.

Novel hybrid architecture
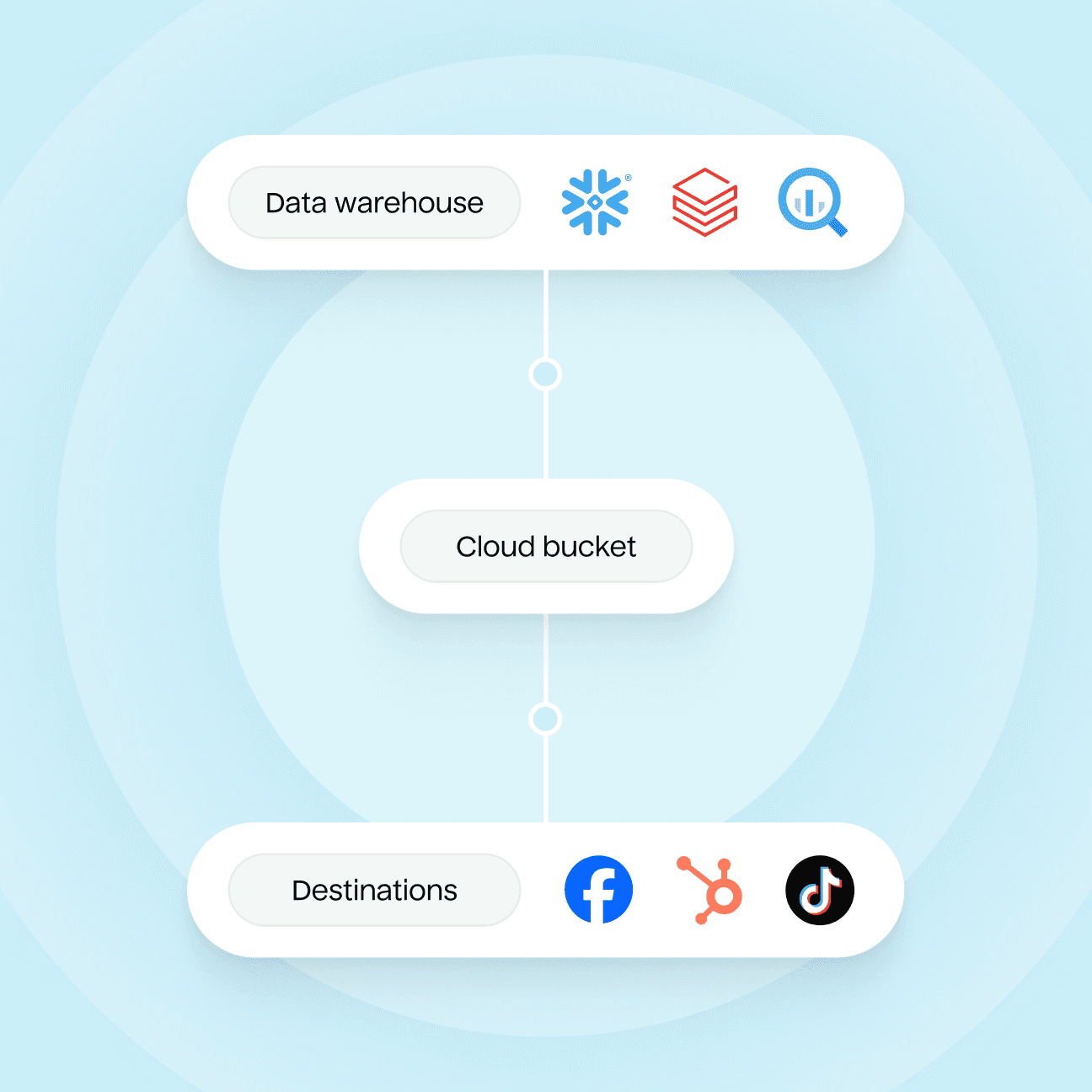
Hightouch never stores any of your data. We believe you should maintain control and take advantage of your existing architecture. Here’s how your data passes through Hightouch:
Hightouch runs queries directly on your warehouse.
You can choose to store all customer data temporarily in your cloud.
Hightouch transfers data to your destination without ever storing it.
Hightouch also supports AWS PrivateLink for Snowflake in certain regions.
Enterprise-ready on day one
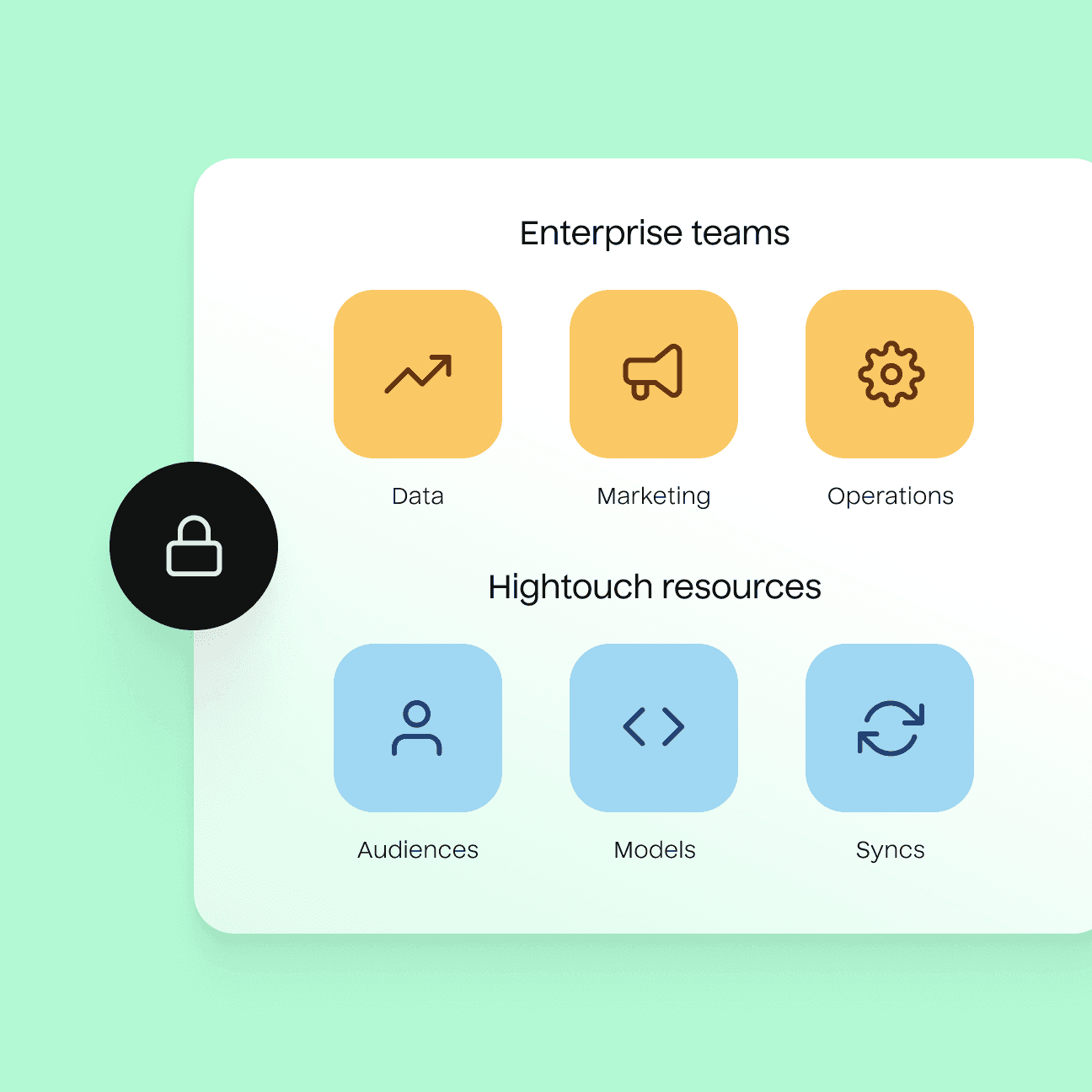
Hightouch provides the control and governance capabilities you need to safely plug Reverse ETL into your tech stack.
SSO: Manage user authentication centrally with SAML SSO and keep access grants up-to-date with support for SCIM.
Role-based access: Leverage fine-grained permissions and custom roles to control who has access to specific workspace resources (models, destinations, and syncs).
Row-level access: Grant users access to data based on geography, business unit, or any other parameter.
Row-level sync controls: Control which data can be synced to each of your destinations, to ensure data only travels to approved tools.
Audit logs: Track, monitor, and search all in-app user activity. Export reports and alerts to your preferred tools.
Approval flows: Require users to receive in-app approval before pushing changes into production. Rollback unintended changes immediately through Git.
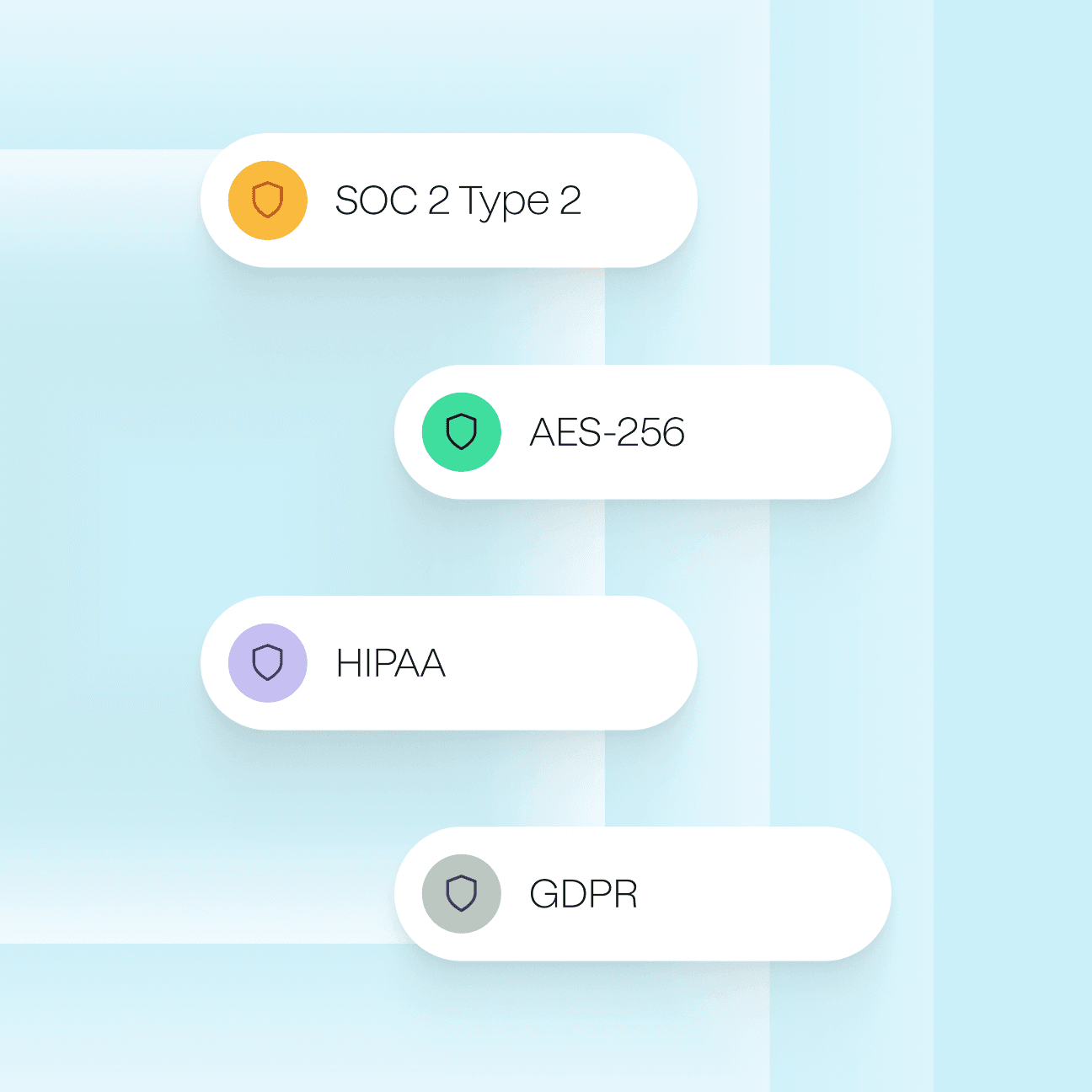
Product security
Our platform architecture and industry compliance certifications mean that your data is always secure.
We complete regular security-design reviews, pen tests using trusted security vendors, and conduct regular audits such as SOC 2 Type 2.
We encrypt all data at rest and protect it in transit with TLS. Hightouch’s metadata database is encrypted by Amazon AWS using standard AES-256 encryption algorithms.
We limit internal access to tools and resources using time-based access.